















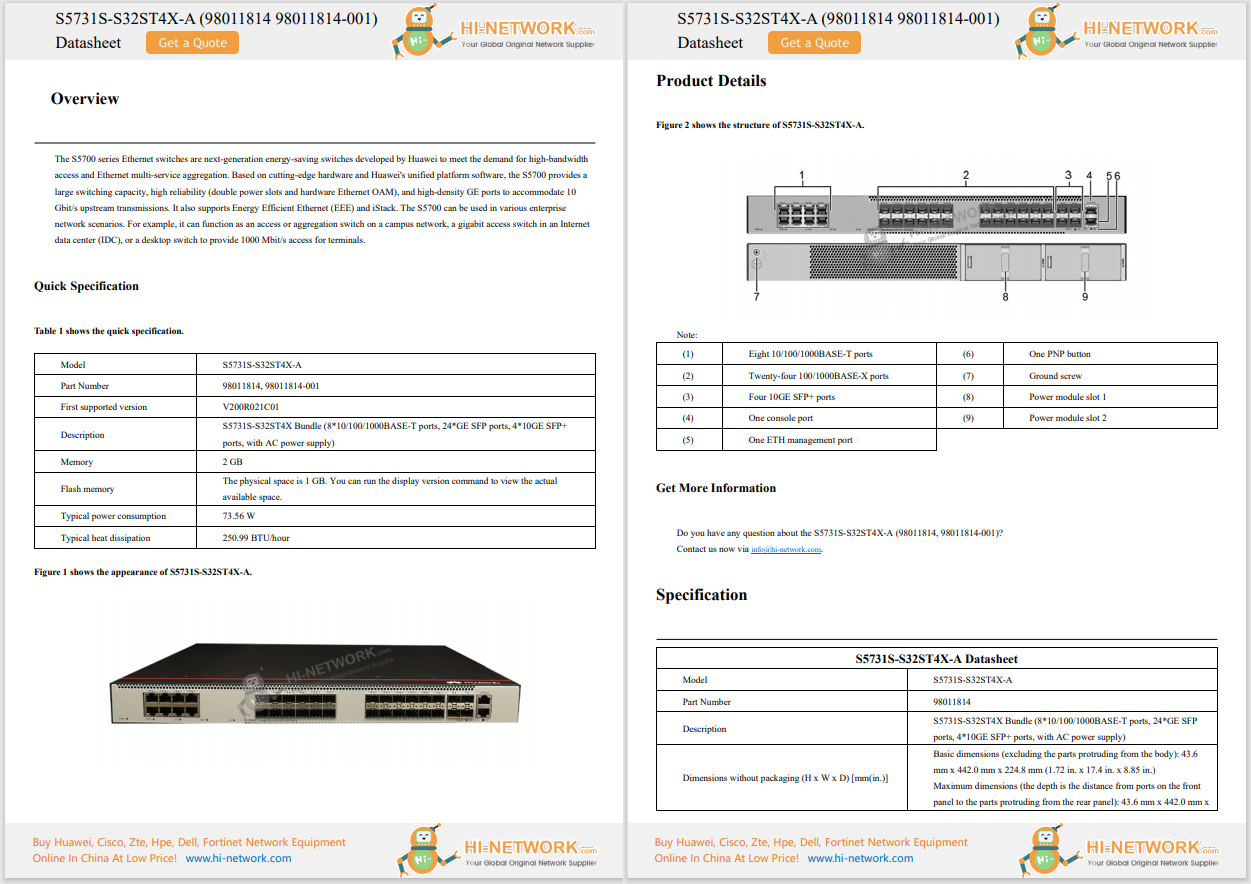










The CISA Zero Trust Capabilities and the Department of Defense (DoD) Zero Trust Capabilities are foundational frameworks developed by U.S. government entities to guide organizations in adopting a Zero Trust security model. As someone who collaborates daily with Cisco's Federal and DoD/Intel teams, I wrote this blog to provide clarity on the similarities and differences between these frameworks -offering insights for Cisco teams and other organizations navigating the complexities of Zero Trust implementation.
While both frameworks share the overarching goal of improving cybersecurity by minimizing implicit trust and continuously verifying user and system identities, they differ in scope, priorities, and operational focus due to the distinct missions and challenges of civilian and defense sectors. This blog helps federal and DoD/Intel agencies, as well as their partners, understand how to tailor their Zero Trust strategies to meet specific operational requirements, compliance mandates, and security objectives.
By analyzing these frameworks side by side, this blog highlights best practices and shows how Zero Trust principles can be applied across diverse environments to enhance resilience against evolving cyber threats. Understanding of the CISA framework helps teams guide civilian agencies and private sector organizations through incremental Zero Trust adoption using flexible Cisco solutions. Meanwhile, DoD expertise supports defense-grade solutions for securing mission-critical environments and addresses advanced adversarial tactics. Ultimately, mastering both frameworks cultivates success for customers across the U.S. public sector and defense landscape.
Below is a detailed analysis of the distinctions and commonalities between the CISA and DoD Zero Trust Capabilities frameworks.
Audience: Primarily targets civilian agencies, federal organizations, state and local governments, and private sector entities within critical infrastructure.
Purpose: Provides a broad, high-level guidance document for transitioning to a Zero Trust architecture across diverse sectors. The goal is to improve cybersecurity posture across the U.S. government and private sector by offering practical steps.
Focus:Generalized for a wide range of users and designed to promote consistency across federal agencies under Executive Order 14028 "Improving the Nation's Cybersecurity".
Audience:Exclusively tailored for the Department of Defense and its associated organizations, including military branches, contractors, and mission-critical systems.
Purpose:A highly detailed and rigorous framework designed to secure classified and unclassified DoD systems against advanced persistent threats (APTs) and adversarial nation-states.
Focus:Defense-specific use cases, mission-critical environments, and national security objectives. The DoD framework includes stringent requirements for protecting sensitive military data and operational infrastructure.
Framework:Based on the NIST 800-207 Zero Trust Architecture Framework, the CISA model translates into practical, incremental guidance tailored to federal agencies' operational needs and maturity levels.
Scope:CISA focuses on five pillars:
Framework:DoD emphasizes end-to-end Zero Trust for classified, unclassified, and operational environments, with a strong focus on adversary tactics and national defense.
Scope:DoD defines 7 pillars of Zero Trust, which are more granular and defense-specific:
Implementation:Provides agencies with a maturity model to track their progress (e.g., traditional, advanced, and optimal Zero Trust maturity levels).
Guidance:Encourages agencies to adopt commercial technologies and follow best practices for securing systems incrementally.
Focus Areas:
Implementation:Requires strict compliance with the DoD Cybersecurity Maturity Model Certification (CMMC) for contractors and adherence to mission-critical security standards.
Guidance:Mandates defense-grade tools, technologies, and protocols (e.g., classified communication networks, advanced threat hunting, and insider threat prevention mechanisms).
Focus Areas:
Risk Tolerance:Designed for environments with varying levels of risk tolerance. Encourages incremental adoption and flexibility based on agency maturity.
Flexibility:A broad and adaptable framework for diverse organizations, including those with limited resources.
Risk Tolerance:Operates with a near-zero risk tolerance due to the critical nature of defense operations. Focuses on eliminating single points of failure and securing the entire ecosystem.
Flexibility:Minimal flexibility due to the rigid requirements for national defense and mission assurance.
To help visualize where these frameworks align -and where they diverge -Table 1 summarizes the key similarities and distinctions between the two.
| Category | CISA Five Pillars of Zero Trust | DoD Seven Pillars of Zero Trust | Key Insights |
| Identify | Identify | User (Identity) | Both emphasize securing user identity, authentication, and access control based on identity verification. |
| Device | Device | Device | Both frameworks include device security and trustworthiness as a key pillar. |
| Network | Network | Network/Environment | Both focus on segmenting and securing network access to reduce attack surfaces. |
| Application/Workload | Application/Workload | Application/Workload | Both include securing applications and workloads through access controls and authentication mechanisms. |
| Data | Data | Data | Both prioritize securing and monitoring data, ensuring proper access controls and encryption. |
| Visibility/Analytics | Not Explicitly Listed | Visibility and Analytics | DoD includes a pillar for analytics and monitoring, while CISA incorporates visibility across all pillars. |
| Automation/Orchestration | Not Explicitly Listed | Automation and Orchestration | DoD adds an explicit pillar for automation, which is implied but not separately listed in CISA's framework. |
Similarities
Both frameworks share a common foundation in securing identity, devices, networks, applications/workloads, and data. They also emphasize the core principles of Zero Trust: "never trust, always verify," least privilege access, and continuous monitoring. Aligned with NIST 800-207, both use its principles as a foundation. While they share similar pillars such as Identity, Device, Network, and Data, the DoD adds more specific categories (e.g., Visibility and Automation).
NIST Special Publication 800-207, titled Zero Trust Architecture (ZTA), is a framework published by NIST that provides guidelines for implementing Zero Trust principles in IT systems. The document serves as a foundational resource for organizations aiming to modernize their cybersecurity defenses and reduce the risk of data breaches and unauthorized access.
Differences
The DoD framework adds two additional pillars for Visibility/Analytics and Automation/Orchestration, emphasizing the need for continuous monitoring and automated responses. CISA incorporates aspects of visibility and automation across its five pillars but does not define them as separate categories.
Table 2: Key Differences of CISA and DoD Zero Trust Models helps clarify the differences with the two frameworks.
| Aspect | CISA Zero Trust | DoD Zero Trust |
| Audience | Civilian agencies, private sector | DoD, military, contractors |
| Scope | Generalized for broad use | Defense-specific and mission-critical |
| Pillars | 5 pillars | 7 pillars |
| Implementation | Incremental, flexible | Strict, rigid |
| Risk Tolerance | Varies | Near-zero |
| Technology Guidance | Encourages commercial solutions | Requires defense-grade solutions |
The CISA and DoD Zero Trust Capabilities represent two complementary approaches to strengthening cybersecurity within the U.S. government. The CISA Zero Trust Capabilities provide a broad, flexible roadmap for implementing Zero Trust in civilian and private sector environments. In contrast, the DoD Zero Trust Capabilities are a highly detailed and stringent framework tailored to the unique requirements of national defense. While both share the common goal of fortifying cybersecurity, their differing levels of detail and focus reflect the distinct operational contexts and priorities of their target audiences.
By comparing these approaches, it becomes evident that both play vital roles in advancing the nation's overall cybersecurity posture. CISA's guidance fosters widespread adoption and consistency across sectors, while the DoD's stringent requirements ensure the highest level of security for critical defense systems. Together, they underscore the importance of Zero Trust as a foundational cybersecurity strategy, adapted to meet the diverse needs of both civilian and defense domains.
To read more about Frameworks and Directives check out Cisco's Modernizing Government Cybersecurity website and its Government Modernization Resources page.
DoD Zero Trust Capability Mapping Cisco and Splunk
 Hot Tags :
Government
Cisco Security Portfolio Frameworks
Hot Tags :
Government
Cisco Security Portfolio Frameworks